
The Stanford Information Networks Group (SING) researches wireless data-centric networks. Currently, much of its work deals with low-power sensor networks, including measuring the behavior of low-power wireless, network protocols and architecture, and operating systems.
Resources
People

Introduction
SWAT (Stanford Wireless Analysis Tool) is a software tool that automates gathering and analysis of network measurements. SWAT provides an interface for configuring experimental parameters in a network. It collects raw packet statistics such as the received signal strength and chip error, and provides modules for calculating and visualizing various metrics derived from these statistics.
SWAT is an open-source, platform-independent tool. The user interface portions and the communication interface between SWAT and the wireless sensor network uses Python. Platform-specific code that runs on the sensor motes is written in nesC, an extension to the C programming language for TinyOS. We use SQL to create the database, making it easy to execute custom queries. The computation intensive component of SWAT is the metric calculation. It consists of a number of python programs, each responsible for computing one metric. SWAT is extensible so users can write their own python modules.
Install SWAT for 802.15.4
Install SWAT for 802.11
Install SWAT for both 802.15.4 and 802.11
Why use SWAT?
-
Benefits of SWAT include, but are not limited to, the following:
How it works
-
SWAT allows researchers to easily gather network data, distill that data into relevant metrics, and visually display the results.
- Enter configuration parameters, testbed information and desired reports
- Users specify the experimental parameters through a configuration UI. These parameters define the settings for which packet and link data will be collected. They include link-layer type (802.15.4/802.11), node list, number of packets, inter-packet interval, type of transmission i.e. broadcast or unicast, CSMA on/off, channel, transmission power, link layer acknowledge-ments on/off, link layer retransmissions on/off (for uni-casts), maximum retransmission count, bit rate (for 802.11), noise sampling on/off and noise sampling rate.
- SWAT runs the experiment for you
- SWAT uses the appropriate interface to program the nodes, send commands and receive packet statistics through a wired or wireless back-channel. SWAT stores the collected data into a database using an SQL server
- SWAT calculates the metrics and displays the reports
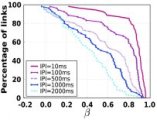
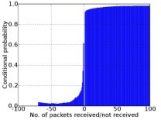
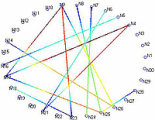
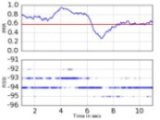
- The reporting UI component allows users to specify which of the supported metrics they would like to calculate from the stored data. SWAT creates reports that consist of the experimental parameters, computed metrics and pertinent figures. Currently, supported metrics include packet delivery temporal and spatial correlations, noise floor distribution, received signal strength to reception ratio correlation, link asymmetries, and reception ratio distribution over time.
Installing swat for 802.11
Minimum System Requirements
Instructions
-
On your host machine:
- Download the OpenWRT source code at http://openwrt.org
- Extract the source code from the tar file
- Download swat_cfg_pkg.tar.gz
- Move the tar file into the OpenWRT root directory, and execute "tar -zxf swat_cfg_pkg.tar.gz"
- You might need to install additional packages. In most cases, you can easily find the package that's missing, but there are a few that are hard to find:
- check that you have installed the "build-essential" package
- ncurses: install "libncurses5-dev"
- GNU awk: install "gawk"
- zlib: install "zlib1g-dev"
- In the OpenWRT root directory, execute "make menuconfig"
- The kernel image is in the bin directory; copy it to the nodes and install the OS
Installing swat for 802.15.4
Minimum System Requirements
Instructions
Installing swat for both 802.15.4 and 802.11
Minimum System Requirements
Instructions
Installing the required packages and creating the SWAT database
To install the MySQL packages on Linux, open a terminal and type the following:
To create the SWAT database on Linux, open a terminal and type the following:
Instructions to install the other required packages:
Running Experiments
- Start the MySQL database
- You must make swat the active database before every run. To do this, open a terminal and type the following:
- sudo mysql (you should see the MySQL command prompt)
- USE swat;
- Start the SWAT backend server
- Open a terminal and run "python webserver.py" from the /swat-code/ui directory
- Open a webrowser and go to localhost:8080
- Configure the experiment parameters (or select a previous configuration) and report options
- Have the node text file ready which includes the node ports and the respective IDs
Downloads
Resources
SWAT Team
- Kannan Srinivasan
- Maria Kazandjieva
- Mayank Jain
- Jung Il Choi
- Edward Kim
- Philip Levis (faculty)
- Juan Batiz-Benet
- Jonathan Chu